WolvCTF2023: YellsAtBefunge
YellsAtBefunge1
There are 3 interesting files given:
befunge.py
chall.py
provided_file.txt
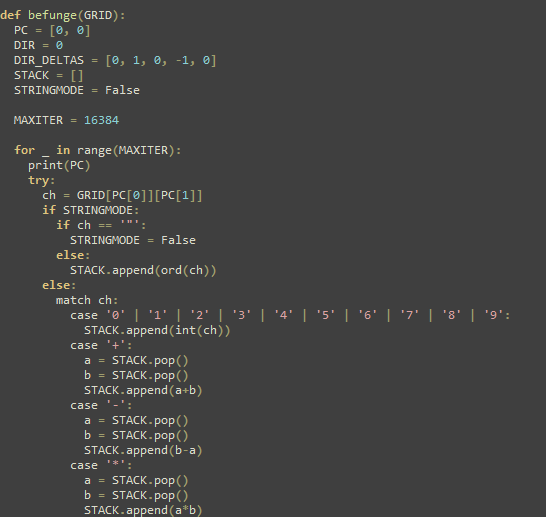
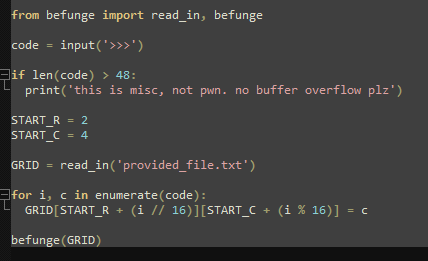
befunge.py looks to be an interpreter for the esolang Befunge . Chall.py gives us the abilty to write to the 3x16 grid enclosed by "#" in 'provided_file.txt'. Looks like the '#' character is a springboard though, moving us multiple tiles.
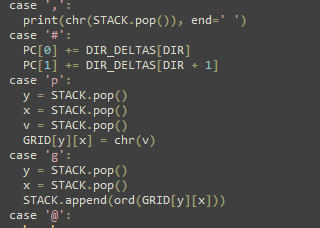
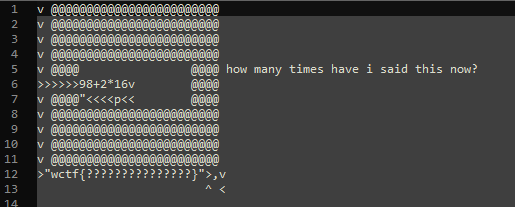
That means we just have to walk into the lower left hand wall; we can enter the string
' v <'which maps to the below result and grabs the flag.
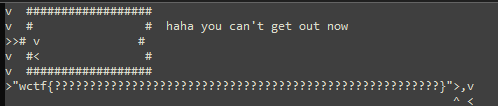
YellsAtBefunge2
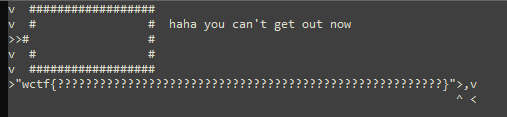
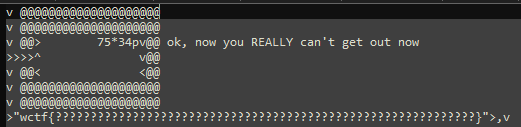
Now the walls actually can't just be walked through; we're going to have to make use of the 'p' opcode, which takes the last 3 values off the stack and write a new character to the grid of instructions; the below program writes a springboard to the location where the inner wall should be, letting us jump over it and grab the flag.
Program Code
After Execution
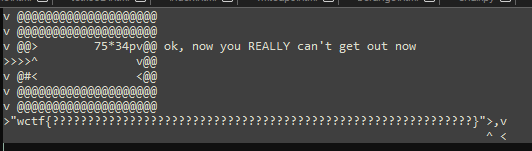
Note the '#' Character written to row 4 column 3. This is inputted at
'> 75*34pv^ v< <'
YellsAtBefunge3
The 'p' opcode has been disabled; that's alright though; we can use the 'g' opcode to read the contents of the grid at an arbitrary point. The below program loops and increments a value in the stack, printing out that column of row 7. Once it hits column 27, the '|' operator at the end of the bottom line will cause the pointer to go down rather than up, hitting a wall and ending the program (this is actually useless in this case though, as an infinite loop would have extracted the flag just as well.)
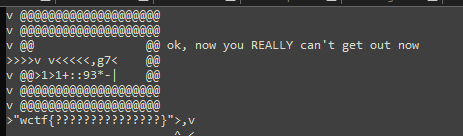
' v v<<<<<,g7< >1>1+::93*-|'
YellsAtBefunge4
Now the 'g' opcode is disabled, and we get exactly 1 use of the 'p' opcode to extract the flag from the below file
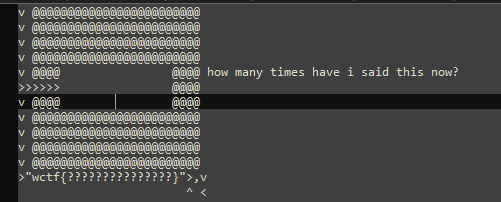
We can do this with a string escape; the " character sends the program into string reading mode, grabbing whatever's in the grid and storing in the stack without executing it until you hit another " character. By placing a " on the outside of the grid with our 1 'p' usage, we can put another one inside and escape.